1 Centralized C&C Deployment SRS-001
As a system admin user, I want to deploy and maintain a central subsystem, called command-and-control (C&C), so that I can update user-exposed settings of subsystems tackling data collection, intrusion detection and prevention.
- Set up host for C&C server.
- Access as root.
- Deploy C&C components following:
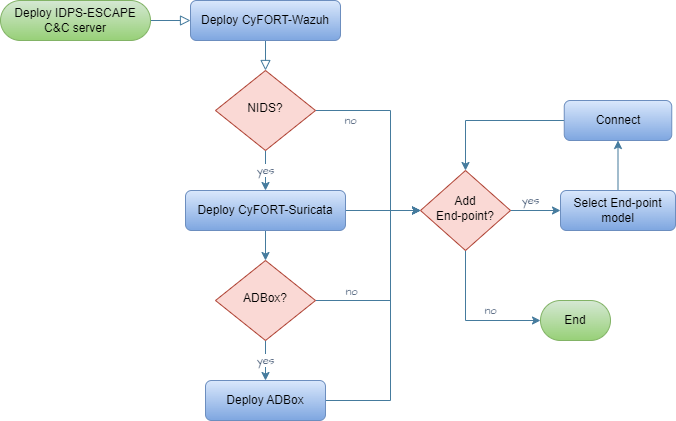
- Configure components via respective software configuration management (SCM) mechanism.
Rationale
To centralize and simplify IDPS components configuration management.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-002 Command & Control
Child links: TST-020 Wazuh installation in a containerized environment
| Attribute | Value |
|---|---|
| importance | 5 |
| urgency | 5 |
| risk | 1 |
| type | F |
| version | 0.1 |
2 Endpoint Status Monitoring SRS-002
As a system admin user, I want to access the end-point monitored system via IDPS-ESCAPE C&C server/unit, so that I can check the status of end-point monitoring solutions deployed, if any.
- Access C&C server as root.
- Via CyFORT-Wazuh manager, list the enrolled agents and their status.
- If deployed, check C-CyFORT-Suricata and mirroring status
- If any deployed, remote connect to endpoint and check local CyFORT-Suricata status.
Rationale
To centralize and simplify agent/sensor configuration management.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-002 Command & Control
| Attribute | Value |
|---|---|
| importance | 5 |
| urgency | 5 |
| risk | 2 |
| type | F |
| version | 0.1 |
3 HIDS Agent Deployment SRS-003
As a sys admin user, I want deploy HIDS agents on the hosts monitored system so that I can enable the IDPS-ESCAPE HIDS capabilities.
- Access host to be monitored
- Install Wazuh Agent
- Enroll Wazuh Agent in CyFORT-Wazuh manager.
- Configure Wazuh Agent.
Rationale
To enable a multi-node deployment of monitoring endpoints host.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-005 Host-based Intrusion Detection
Child links: TST-021 Wazuh agent installation and enrollment: the local machine
| Attribute | Value |
|---|---|
| importance | 5 |
| urgency | 5 |
| risk | 1 |
| type | F |
| version | 0.1 |
4 HIDS Agent Management SRS-004
As a sys admin user, I want to enabled/disabled HIDS agents deployed on the host monitored system.
- Access C&C server
- Enroll/unenroll Wazuh Agent from CyFORT-Wazuh manager
- Possibly, remove logs and config files.
Rationale
To enable system hosts security posture monitoring
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-005 Host-based Intrusion Detection
Child links: TST-023 Wazuh agent deletion and uninstallation, TST-024 Wazuh agent unenrollment
| Attribute | Value |
|---|---|
| importance | 5 |
| urgency | 5 |
| risk | 2 |
| type | F |
| version | 0.1 |
5 Network Monitoring Control SRS-005
As a sys admin user, I want to enable/disable network monitoring within IDPS-ESCAPE subsystem boundaries.
- Access C&C server
- Deploy C-CyFORT-Suricata
- Set up channel to be connections to be monitored
- Possibly, add custom rules.
Rationale
To enable traffic monitoring
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-006 NIDS Support
| Attribute | Value |
|---|---|
| importance | 5 |
| urgency | 4 |
| risk | 2 |
| type | F |
| version | 0.1 |
6 Centralized NIDPS Prevention SRS-006
As a sys admin user, I want a centralized NIDPS in the C&C server.
- Access C&C server
- Deploy C-CyFORT-Suricata
- Activate prevention in the config and set up actions behavior.
Rationale
To be able to take reactive corrective measures and mitigate intrusions
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-007 Intrusion Prevention
| Attribute | Value |
|---|---|
| importance | 2 |
| urgency | 1 |
| risk | 4 |
| type | F |
| version | 0.1 |
7 Raw Traffic Capture SRS-007
As a sys admin user, I want to capture and forward raw network traffic to the C&C server, to run NIDS on such a traffic.
- Access C&C server.
- Deploy C-CyFORT-Suricata.
- Identify host capture interface (CI), C&C CI and IP.
- Run port mirroring activation script with above arguments.
Rationale
To collect events for threat hunting and CTI operations, reducing the NIDS overhead and to do customized AD.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-008 Network Capture Forwarding
Child links: TST-026 Port mirroring for remote machines
| Attribute | Value |
|---|---|
| importance | 5 |
| urgency | 5 |
| risk | 2 |
| type | F |
| version | 0.1 |
8 Dockerized NIDS Deployment SRS-008
As a sys admin user, I want to deploy NIDS components as a Docker container on a system end-points hosts, to monitor traffic and store logs locally.
- Access end-point (EP) host,
- Deploy using custom script.
- Update the configs file (.yml) with local configuration.
Rationale
To ensure the following properties: consistent and reproducible environments, isolation, resource efficiency, scalability, portability, fast spawning and shutdown, improved CI/CD, support of micro services architecture, improved dependency management.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-009 Docker Deployment Option
Child links: TST-019 Suricata installation in a containerized environment
| Attribute | Value |
|---|---|
| importance | 3 |
| urgency | 2 |
| risk | 2 |
| type | F |
| version | 0.1 |
9 Signature-Based HIDS SRS-009
As a sys admin user, I want to enable host intrusion detection via pattern matching with known/expected threats (signature-based HIDS).
- Access host to be monitored.
- Deploy Wazuh Agent (using C&C manager ip).
- Enroll Agent agent.
- Set up local configs and logs.
- Possibly, define custom rules.
Rationale
To build on the mature and existing rule-based detection and CTI body of knowledge and to mitigate low AD detection risk.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-011 Signature-based Host IDS
| Attribute | Value |
|---|---|
| importance | 5 |
| urgency | 5 |
| risk | 1 |
| type | F |
| version | 0.1 |
10 Centralized Threat Management SRS-010
As SOC member user, I want to manage the HIDP and NIDS results and information jointly, to have a centralized overview of the system for threat detection, investigation, and response.
- Access C&C server
- Deploy CyFORT-Wazuh and HIDS agents
- Deploy (C-)CyFORT-Suricata
- Integrate CyFORT-Suricata and CyFORT-Wazuh using custom script and procedure
Rationale
None
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-012 XDR & SIEM Integration
Child links: TST-025 Suricata and Wazuh Integration
| Attribute | Value |
|---|---|
| importance | 5 |
| urgency | 4 |
| risk | 1 |
| type | F |
| version | 0.1 |
11 Network Event Visualization SRS-011
As SOC member, I want a graphic visualization of the network events detected in my system.
Assuming: CyFORT-Suricata integrated in CyFORT-Wazuh
- Access CyFORT-Wazuh Dashboard
- Filter security events generate by NIDS group rules
Rationale
To improve accessibility and easy-of-use for IDPS-ESCAPE end-users
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-013 Visual Dashboard
Child links: TST-027 Traffic monitoring on Wazuh (local), TST-028 Traffic monitoring on Wazuh (remote), TST-032 Wazuh filters using the Wazuh Dashboard
| Attribute | Value |
|---|---|
| importance | 3 |
| urgency | 3 |
| risk | 1 |
| type | F |
| version | 0.1 |
12 Host Event Visualization SRS-012
As SOC member, I want a graphic visualization of the host events detected in my system.
Assuming: CyFORT-Wazuh and HIDS agents deployed
- Access CyFORT-Wazuh Dashboard
- Filter security events generate by HIDS group rules
Rationale
To improve accessibility and easy-of-use for IDPS-ESCAPE end-users
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-013 Visual Dashboard
| Attribute | Value |
|---|---|
| importance | 3 |
| urgency | 3 |
| risk | 1 |
| type | F |
| version | 0.1 |
13 HIDS Agent Status Panel SRS-013
As SOC member, I want to check the status of HIDS agents.
Assuming: CyFORT-Wazuh and HIDS agents deployed and enrolled to C&C Manager
- Access CyFORT-Wazuh Dashboard.
- Look dedicated panel and click to the agent ID for additional info.
Rationale
To improve IDPS-ESCAPE status management for the end-users
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-013 Visual Dashboard
| Attribute | Value |
|---|---|
| importance | 3 |
| urgency | 2 |
| risk | 1 |
| type | F |
| version | 0.1 |
14 Event Decoding & Transformation SRS-014
As SOC member, I want the detected event to be correctly decoded and transformed before usage and storage.
- Access C&C server
- Access CyFORT-Wazuh manager
- Run testing and verification of rules and decoders via CyFORT-Wazuh server API
Rationale
To ensure avoid errors and inaccuracy
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-014 Data Extraction API
| Attribute | Value |
|---|---|
| importance | 3 |
| urgency | 1 |
| risk | 1 |
| type | F |
| version | 0.1 |
15 Custom Rule Support SRS-015
As a user, I want my SIEM to interpret a new type of data forwarded by agents/sensors.
- Access C&C server
- Access CyFORT-Wazuh manager
- Add custom rules and custom decoders.
Rationale
To extend the detection capability of IDPS-ESCAPE and tailor the detection to my system
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-014 Data Extraction API
| Attribute | Value |
|---|---|
| importance | 2 |
| urgency | 1 |
| risk | 3 |
| type | F |
| version | 0.1 |
16 Indexer Credential Management SRS-016
As an admin user, I want to modify the credentials of data indexer for a user, to improve the security level of the admin password.
- Access C&C server
- Access CyFORT-Wazuh manager
- Update
config/wazuh_indexer/internal_users.ymlfile.
Rationale
Maintain/improve the security of IDPS-ESCAPE
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-015 Software Configuration Management
Child links: TST-029 Changing password for Wazuh indexer users, TST-030 Changing password for Wazuh API users
| Attribute | Value |
|---|---|
| importance | 3 |
| urgency | 1 |
| risk | 2 |
| type | F/S |
| version | 0.1 |
17 Custom Data Source SRS-017
As a user, I want to define a ADBox to fetch data from an indexer at specific host address.
- Access C&C server
- Access ADBox
- Modify IP address in
../siem_mtad_gat/assets/secrets/wazuh_credentials.json
Rationale
To connect ADBox to a specific data source containing data of interest, possibly different from the default one
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-015 Software Configuration Management
Child links: TST-034 ADBox set up indexer host address
| Attribute | Value |
|---|---|
| importance | 5 |
| urgency | 4 |
| risk | 4 |
| type | F |
| version | 0.1 |
18 ML Hyperparameter Tuning SRS-018
As a user, I want to modify the default hyperparameter of ML methods used by ADBox.
- Access C&C server
- Access ADBox
- Modify values in
siem_mtad_gat/assets/default_configs/mtad_gat_train_config_default_args.json
Rationale
To globally tune ML algorithm to a specify system/scenario
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-015 Software Configuration Management
Child links: LARC-012 ADBox ConfigManager
| Attribute | Value |
|---|---|
| importance | 3 |
| urgency | 2 |
| risk | 2 |
| type | F |
| version | 0.1 |
19 Datatype Transformation Map SRS-019
As a user, I want to modify the datatype transformation map operated by ADBox on fetched.
- Access C&C server
- Access ADBox
- Modify key values
../siem_mtad_gat/assets/wazuh/wazuh_columns.json
Rationale
To maintain the consistency with SIEM solution
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-015 Software Configuration Management
| Attribute | Value |
|---|---|
| urgency | 1 |
| type | F |
| version | 0.1 |
20 Ingestion Field Update SRS-020
As a user, I want to update the default fields fetched at ingestion phase by ADBox.
- Access C&C server
- Access ADBox
- Update key and values in
../siem_mtad_gat/assets/wazuh/wazuh_columns.json
Rationale
To maintain the consistency with SIEM solution, add custom feature
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-015 Software Configuration Management
| Attribute | Value |
|---|---|
| urgency | 1 |
| type | F |
| version | 0.1 |
21 Default Use Case Update SRS-021
As a user, I want to update the default use case of ADBox.
- Access C&C server
- Access ADBox
- Modify
../siem_mtad_gat/assets/default_configs/default_detector_input_config.json
Rationale
To adapt ADBox default behavior
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-015 Software Configuration Management
Child links: LARC-012 ADBox ConfigManager
| Attribute | Value |
|---|---|
| importance | 3 |
| urgency | 3 |
| risk | 1 |
| type | F |
| version | 0.1 |
22 Indexer Credentials Update SRS-022
As a user, I want to update indexer credentials in ADBox.
- Access C&C server
- Access ADBox
- Update CyFORT-Wazuh indexer credentials in
../siem_mtad_gat/assets/secrets/wazuh_credentials.json
Rationale
To adapt to local configuration
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-015 Software Configuration Management
Child links: TST-035 ADBox change indexer credentials
| Attribute | Value |
|---|---|
| importance | 3 |
| urgency | 3 |
| risk | 2 |
| type | F |
| version | 0.1 |
23 Agent Registration Process SRS-023
As a user, I want to register a new agent in the central SIEM&XDR.
Assuming the CyFORT-Wazuh Manager is running on C&C and an agent is running on the selected host, either:
a. Add the manager IP as an environment variable during the agent installation process.
b. Set the manager IP in the agent configuration file.
c. Requests the key from the manager API and manually imports it into the agent.
Rationale
To enable a non-static configuration of monitored nodes.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-016 Agent (De)Registration
Child links: TST-022 Wazuh agent installation and enrollment: remote machine
| Attribute | Value |
|---|---|
| importance | 3 |
| urgency | 3 |
| risk | 1 |
| type | F |
| version | 0.1 |
24 Event Querying Capability SRS-024
As a user, I want to run queries on data such as events, alerts and statistics.
Assuming: CyFORT-Wazuh running and established connection to indexer
- Formulate query as Wazuh Query Language
- Query to indexer via Wazuh API
Rationale
To achieve a programmatic access to security alert and event data.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-018 Data Management Subsystem
Child links: TST-031 Wazuh filters using the RESTful API
| Attribute | Value |
|---|---|
| importance | 2 |
| urgency | 4 |
| risk | 1 |
| type | F |
| version | 0.1 |
25 MITRE ATT&CK Mapping SRS-025
As a user, I want to map a detected event to the MITRE ATT&CK framework.
Assuming: CyFORT-Wazuh running
- Open the document corresponding to the event (e.g. via index query, or using the dashboard)
- Check if the following keys exist in the attributes
rule.mitre.id , rule.mitre.tactic , rule.mitre.technique
Rationale
To improve and speed up threat detection and classification, thereby facilitating CTI analysis.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-023 MITRE ATT&CK Mapping
Child links: TST-036 Map a detected event to MITRE ATT&CKS
| Attribute | Value |
|---|---|
| importance | 2 |
| urgency | 2 |
| risk | 1 |
| type | F |
| version | 0.1 |
26 TIP Data Export SRS-026
As a user, I want to export data from IDPS-ESCAPE to a TIP.
Rationale
To enable programmatic access, which would also in turn support integration with SATRAP-DL.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-025 Threat Detection API
| Attribute | Value |
|---|---|
| urgency | 1 |
| type | F |
| version | 0.1 |
27 ML-Based Anomaly Detection SRS-027
As a system admin, I want to run a machine learning algorithm to detect anomalous behaviors within my system.
- Access C&C server
- Access ADBox
- Select a trained detector
- Run a prediction script using the chosen detection either for a selected time interval or in real time.
Rationale
None
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-030 Deep Learning Technique
Child links: TST-007 ADBox use case 1 with a Wazuh connection, TST-008 ADBox use case 1 without a Wazuh connection, TST-011 ADBox use case 3 with a Wazuh connection, TST-012 ADBox use case 3 without a Wazuh connection, LARC-008 ADBox batch and real-time prediction flow, LARC-020 SONAR detection pipeline sequence
| Attribute | Value |
|---|---|
| importance | 5 |
| urgency | 4 |
| risk | 2 |
| type | F |
| version | 0.1 |
28 Algorithm Comparison Feature SRS-028
As a user, I want to compare the outcome of different anomaly detection algorithms on my data.
Assuming: Two different algorithms A1 and A2 available in ADBox, and two compatible detectors D1 and D2 based on these algorithms, respectively.
- Access C&C server
- Access ADBox
- Establish detection parameters (time interval, features, etc.)
- Select a (trained) detector D1 using algorithm A1
- Run a prediction script using D1.
- Select a (trained) detector D2 using algorithm A2
- Run a prediction script using D2.
- Compare output using dedicated Dashboard.
Rationale
To validate the AD capabilities.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-031 Multiple ML Techniques
| Attribute | Value |
|---|---|
| importance | 2 |
| urgency | 1 |
| risk | 1 |
| type | F |
| version | 0.1 |
29 Host & Network Ingestion SRS-029
As a user, I want to ingest and transform data generated from both host and network events to feed anomaly detectors.
- Access C&C server
- Access ADBox
- Set up data ingestion and transformation of data derived from CyFORT-Wazuh and CyFORT-Suricata logs arguments.
Rationale
To enable holistic system monitoring.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-032 Host and Network Ingestion
Child links: LARC-003 ADBox preprocessing flow
| Attribute | Value |
|---|---|
| importance | 4 |
| urgency | 4 |
| risk | 1 |
| type | F |
| version | 0.2 |
30 AD Results Visualization SRS-030
As a user, I want to read/plot AD results of training and test data.
Assuming: trained detector with unique identifier uuid available.
- Access C&C server
- Access ADBox
- Open the folder
siem_mtad_gat/assets/detector_models/uuid/training - Use either external tools or viz-notebooks to visualize
- train subset AD output:
train_output.pkl- test subset AD output:test_output.pkl
Rationale
To enable programmatic use of such data to further elaborate and evaluate output of training
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-034 Standardized AD Output
Child links: TST-037 Open prediction file of training data
| Attribute | Value |
|---|---|
| importance | 2 |
| urgency | 2 |
| risk | 2 |
| type | F |
| version | 0.1 |
31 Training Loss Visualization SRS-031
As a user, I want to read/plot losses of training and test data.
Assuming: trained detector with unique identifier uuid available.
- Access C&C server
- Access ADBox
- Open the folder
siem_mtad_gat/assets/detector_models/uuid/training - Use either external tools or viz-notebooks to visualize
- train :
train_losses.png- test :test_losses.png
Rationale
To evaluate quality of output of training
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-034 Standardized AD Output
Child links: TST-038 Visualize train losses
| Attribute | Value |
|---|---|
| importance | 1 |
| urgency | 1 |
| type | F |
| version | 0.1 |
32 Predicted Anomalies Visualization SRS-032
As a user, I want to read/plot the list of predicted anomalies .
Assuming: trained detector with unique identifier uuid available, use-case scenario uc-x given.
- Access C&C server
- Access ADBox
- Within
siem_mtad_gat/assets/detector_models/uuid/predictionfolder, open:uc-x_predicted_anomalies_data-*.json
Rationale
To enable programmatic use of such data to further elaborate and evaluate output of prediction
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-034 Standardized AD Output
Child links: TST-039 Open prediction raw outcome
| Attribute | Value |
|---|---|
| importance | 4 |
| urgency | 3 |
| risk | 1 |
| type | F |
| version | 0.1 |
33 Remote Endpoint Deployment SRS-033
As a system admin user, I want to deploy IDPS end-point monitoring solutions on a remote end-point by choosing from multiple configuration options so that I can monitor events on my system's edge/endpoints.
- Access end-point as root.
- Deploy end-point components following:
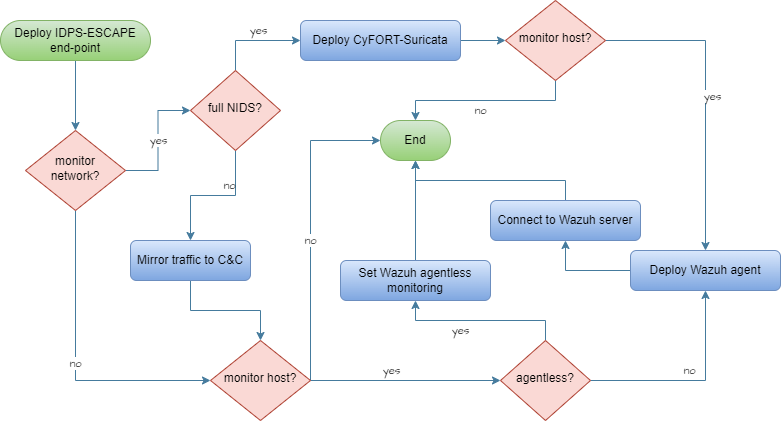
- Connect local solution to C&C sub-system.
Rationale
To adapt and improve performance
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-037 Multiple Deployment Models
Child links: LARC-004 IDPS-ESCAPE end-point integrated arch., LARC-005 IDPS-ESCAPE end-point hybrid arch., LARC-006 IDPS-ESCAPE end-point host-only IDS arch., LARC-007 IDPS-ESCAPE end-point capture-only arch.
| Attribute | Value |
|---|---|
| importance | 5 |
| urgency | 4 |
| risk | 3 |
| type | F |
| version | 0.1 |
35 Offline Anomaly Detection SRS-035
As I user, I want to perform off-line AD on a SIEM data registered by Wazuh on date YYYY-MM-DD.
Assuming: trained detector with unique identifier uuid available.
- Access C&C server
- Access ADBox
- Add an use-case file
siem_mtad_gat/assets/drivers/uc_x.yamlincluding
yaml
prediction:
run_mode: "historical"
index_date: YYYY-MM-DD
detector_id: uuid
Rationale
To detect anomalies without real-time obstacles and possibly after pre-selection, and to review events from the past investigating a possible threat
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-039 Offline AD
Child links: TST-009 ADBox use case 2 with a Wazuh connection, TST-010 ADBox use case 2 without a Wazuh connection, LARC-002 ADBox historical data prediction pipeline flow, LARC-020 SONAR detection pipeline sequence
| Attribute | Value |
|---|---|
| importance | 4 |
| urgency | 4 |
| risk | 2 |
| type | F |
| version | 0.1 |
36 Custom NIDS Rules SRS-036
As user, I want to add a new custom rule set signature to a specific network related event type.
- Access C&C server
- Add the file with custom rules
local.rules -
Open
/etc/suricata/suricata.yamland update:rule-files: - suricata.rules - /path/to/local.rules
Rationale
To extend the detection capability of IDPS-ESCAPE and tailor the detection to my system
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-040 Signature-Based NIDS
| Attribute | Value |
|---|---|
| importance | 3 |
| urgency | 1 |
| risk | 3 |
| type | F |
| version | 0.1 |
37 Anomaly-Based NIDS SRS-037
As a user, I want to find anomalies in the network traffic to detect threats not recognized by the signature-based NIDS.
Assuming: CyFORT-Suricata integrated with CyFORT-Wazuh
- Access C&C server
- Access ADBox
- Add an use-case file
siem_mtad_gat/assets/drivers/uc_x.yamlincluding as features attributes from Suricataeve.logdecoding - Run ADBox
Rationale
None
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-004 Multivariate Anomaly Detection
Child links: TST-015 ADBox use case 5 with a Wazuh connection, TST-016 ADBox use case 5 without a Wazuh connection
| Attribute | Value |
|---|---|
| status | To detect deviations from an a priori normal baseline system behavior, possibly caused by malicious actors. |
| importance | 4 |
| urgency | 3 |
| risk | 1 |
| type | F |
| version | 0.1 |
38 Joint Host-Network Training SRS-038
As a user, I want to train a detector to detect anomaly by using both host and network events.
- Access C&C server
- Access ADBox
- Train a detector using features derived from CyFORT-Wazuh and CyFORT-Suricata logs arguments.
Rationale
None
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-030 Deep Learning Technique
Child links: LARC-001 ADBox training pipeline flow, TST-013 ADBox use case 4 with a Wazuh connection, TST-014 ADBox use case 4 without a Wazuh connection, LARC-019 SONAR training pipeline sequence
| Attribute | Value |
|---|---|
| importance | 5 |
| urgency | 4 |
| risk | 2 |
| type | F |
| version | 0.1 |
39 Algorithm Selection Option SRS-039
As a user, I want to be able to select the algorithm to use for AD to run AD according to the most suitable AD principle.
- Access C&C server
- Access ADBox
- Select the ML-package to be used by the training/test pipelines.
Rationale
Adapt AD functionality to different scenarios and maximize accuracy.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-031 Multiple ML Techniques
Child links: LARC-009 ADBox machine learning package
| Attribute | Value |
|---|---|
| status | unavaliable |
| importance | 3 |
| urgency | 2 |
| risk | 2 |
| type | F |
| version | 0.1 |
40 Data Management Subpackage SRS-040
ADBox should include a Data Management subpackage, centralizing data storage, retrieval and all other operation concerning the management of data along the AD pipelines.
Rationale
To consolidate the data management operation
Acceptance criteria
Code inspection
Parent links: MRS-004 Multivariate Anomaly Detection
Child links: LARC-010 ADBox data manager
| Attribute | Value |
|---|---|
| importance | 3 |
| urgency | 3 |
| risk | 3 |
| type | A |
| version | 0.1 |
41 Time Management Package SRS-041
ADBox should include a Time Management package, handling various aspects of time-related operations given the time-series based approach.
Rationale
To consolidate the time management operation
Acceptance criteria
Code inspection
Parent links: MRS-004 Multivariate Anomaly Detection
Child links: LARC-011 ADBox TimeManager
| Attribute | Value |
|---|---|
| importance | 3 |
| urgency | 2 |
| risk | 2 |
| type | A |
| version | 0.1 |
42 Prediction Shipping Feature SRS-042
As a user, I want the prediction of the anomaly detection subsystem to be shipped to the central indexer.
Assuming:
-
CyFORT-Wazuh and ADBox deployed
-
a use case, including training settings available.
- Build ADBox container
- Run ADBox training with the shipping flag enabled
- When using the created detector, turn the shipping on.
Rationale
Centralization and integration of information
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-018 Data Management Subsystem
Child links: TST-018 ADBox Create detector data stream, LARC-013 ADBox RequestResponseHandler, LARC-014 ADBox Shipper, LARC-020 SONAR detection pipeline sequence
| Attribute | Value |
|---|---|
| importance | 2 |
| urgency | 2 |
| risk | 2 |
| type | F |
| version | 0.1 |
43 AD Data Visualization SRS-043
As a user, I want a graphic visualization of the data produced by the anomaly detection subsystem.
Assuming:
-
CyFORT-Wazuh and ADBox deployed and integrated
-
At least a detector data stream available in CyFORT-Wazuh Indexer
- Open CyFORT-Wazuh
- Add the detector's pattern to Dashboard pattern list.
- (Optional) Create an ad hoc visualization and a Dashboard.
Rationale
Accessibility of AD data for the end-users and centralise forensics
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-017 Monitoring Frontend
Child links: TST-033 ADBox Wazuh integration Dashboard
| Attribute | Value |
|---|---|
| importance | 2 |
| urgency | 2 |
| risk | 2 |
| type | F |
| version | 0.1 |
44 Platform-Independent Deployment SRS-044
As a user, I want to deploy ADBox using a platform-independent solution, and to further develop it.
Assuming:
- CyFORT-Wazuh deployed
- Deploy ADBox using dev container.
Rationale
Ensure cross-platform compatibility and portability both for usage and develpment.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-020 Platform Independence
Child links: TST-003 Install ADBox as dev container
| Attribute | Value |
|---|---|
| importance | 4 |
| urgency | 4 |
| risk | 2 |
| type | F/A |
| version | 0.1 |
45 High-Level Architecture Overview SRS-045
As a user, I want to understand IDPS-ESCAPE high level architecture.
Assuming:
- access to idps-escape docs repository
- Open the
docs\specsproject folder. - Open HARC
Rationale
To follow a consistent and well-defined process, while improving development security.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-026 C5-DEC Development Model
Child links: TST-040 Visualize IDPS-ESCAPE high level architecture
| Attribute | Value |
|---|---|
| urgency | 3 |
| risk | 1 |
| type | S |
| version | 0.1 |
46 Cross-Platform ADBox Deployment SRS-046
As a user, I want to deploy ADBox as a platform independent solution.
Assuming:
- CyFORT-Wazuh deployed
- Deploy ADBox via Docker and shell scripts.
Rationale
Ensure cross-platform compatibility and portability for usage.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-020 Platform Independence
Child links: TST-001 Deploy ADBox via Docker and shell scripts
| Attribute | Value |
|---|---|
| importance | 5 |
| urgency | 5 |
| risk | 2 |
| type | F |
| version | 0.1 |
47 Interactive Use Case Builder SRS-047
As a user, I want to interactively compile a use case, to create an anomaly detector and run predictions.
- Access C&C server
- Access ADBox
- Run interactive shell.
Rationale
To simplify the process of preparing use-case files.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-030 Deep Learning Technique
Child links: TST-004 Run ADBox console
| Attribute | Value |
|---|---|
| urgency | 2 |
| type | F |
| version | 0.1 |
48 Default Detector Training SRS-048
As a user, I want to train a base detector using default parameters.
- Access C&C server
- Access ADBox
- ADBox with default option.
Rationale
To obtain a detector without use case specification.
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-030 Deep Learning Technique
Child links: TST-005 Run ADBox in default mode with a Wazuh connection, TST-006 Run ADBox in default mode without a Wazuh connection, LARC-019 SONAR training pipeline sequence
| Attribute | Value |
|---|---|
| importance | 2 |
| urgency | 2 |
| risk | 1 |
| type | F |
| version | 0.1 |
49 Anomaly Shipping to Indexer SRS-049
As a user, I want to enable the shipping of anomaly detection outcomes to the central indexer to centralize data anaysis and threat hunting.
- Access Command and Control server.
- Access ADBox.
- Run shipping installation script.
Rationale
To ensure consisten integration of AD outcomes with SIEM
Acceptance criteria
Successful validation according to the corresponding test case specification
Parent links: MRS-021 IaC Deployment
Child links: TST-017 ADBox shipping install
| Attribute | Value |
|---|---|
| importance | 3 |
| urgency | 3 |
| risk | 2 |
| type | F |
| version | 0.1 |
50 Insider Threat Detection and Prevention: Data exfiltration SRS-050
As a security engineer,
I want RADAR to detect high-volume file read/copy behavior on endpoints and automatically trigger a host active response mitigations with a clear audit trail.
- RADAR shall emit an Insider Threat alert when the per-user anomaly detection model classifies current file-access activity as abnormal, i.e. when observed read volume and/or copy indicators exceed the user’s learned baseline in RRCF model.
- The alert includes user/host context, anomaly score and confidence, and timestamp period.
- The Wazuh Monitor sends the alert to webhook upon passing the value of risk threshold defined per the RADAR Technical Specification:
- RADAR’s active response system is designed around a risk-aware tiering model that integrates statistical detection results with contextual scenario severity. Instead of relying on static or arbitrary thresholds, the framework interprets anomaly scores through the lens of a Risk = Likelihood × Impact formulation, allowing it to react proportionately to the threat level of each event.
- If passed the threshold, the active response executes the configured agent active responses: logging of events for the anomalous period, and user lock on the host. In the case if the computed risk score is below the threshold, the alert is logged in the index.
- The records of active responses are logged.
Rationale
Detecting massive reads and copy indicators is a reliable early sign of data exfiltration, converting these signals into a single scored alert lets us enforce the risk threshold and automatically apply agent-level containment.
Acceptance criteria
Successful validation according to the corresponding test case specification.
Parent links: MRS-007 Intrusion Prevention
Child links: LARC-015 RADAR scenario setup flow, LARC-016 RADAR active response flow, LARC-017 RADAR integration with Opensearch modules, LARC-018 RADAR logical flow
| Attribute | Value |
|---|---|
| importance | 4 |
| urgency | 3 |
| risk | 2 |
| type | F |
| version | 0.4 |
51 Suspicious login Detection and Prevention: Impossible travel and Failed-login bursts SRS-051
As a security engineer, I want RADAR to detect suspicious login activity (failed-login bursts and impossible travel) and apply the existing risk policy to contain the attack.
- RADAR shall emit a Suspicious Login alert when rule-based conditions classify the current authentication pattern as abnormal. Concretely, we flag: (i) a failed-login burst—≥5 failed attempts for the same user within 60 seconds; (ii) impossible travel—a successful login with a country change and computed geo-velocity ≥ 900 km/h; and (iii) a correlation rule where a failed-login burst is followed by an impossible-travel success for the same user within a short window (e.g., 5 minutes). These rules operate alongside the AD pipeline but provide deterministic, immediate detection.
- The alert carries the user/host context, anomaly score and confidence, and time window.
- The Wazuh Monitor sends the alert to webhook upon passing the value of risk threshold.
- If passed the threshold, RADAR triggers the configured actions on agent: logging of events for the anomalous period, user lock on the SSO, and firewall block. In the case if the computed risk score is below the threshold, the alert is logged in the index.
- The records of active responses are logged.
Rationale
Rapid failed-login bursts and impossible-travel logins are strong indicators of credential compromise, aggregating them into a scored alert with triggered containment enables risk-based actions.
Acceptance criteria
Successful validation according to the corresponding test case specification.
Parent links: MRS-007 Intrusion Prevention
Child links: TST-042 RADAR: build suspicious login, TST-050 RADAR: build suspicious login, LARC-015 RADAR scenario setup flow, LARC-016 RADAR active response flow, LARC-017 RADAR integration with Opensearch modules, LARC-018 RADAR logical flow
| Attribute | Value |
|---|---|
| importance | 4 |
| urgency | 3 |
| risk | 2 |
| type | F |
| version | 0.4 |
52 DDoS Detection and Prevention: SYN-flood SRS-052
As a security engineer, I want RADAR to detect inbound traffic surges consistent with DDoS against protected services and output the configured mitigation with auditable evidence.
- RADAR shall emit a DDoS alert when the per-endpoint anomaly detection model flags the current traffic profile as anomalous relative to the endpoint’s learned baseline.
- The alert includes the user/host context, anomaly score and confidence, and time window.
- The Wazuh Monitor sends the alert to webhook upon passing the value of risk threshold.
- If passed the threshold, RADAR produces the mitigation output wired for this scenario: firewall block and rate-limiting of the host connections. In the case if the computed risk score is below the threshold, the alert is logged in the index.
- The records of active responses are logged.
Rationale
Sudden traffic surges against a protected service are a practical indicator of DDoS, turning this into a scored alert enables the risk threshold to trigger mitigations with auditable records.
Acceptance criteria
Successful validation according to the corresponding test case specification.
Parent links: MRS-007 Intrusion Prevention
Child links: LARC-015 RADAR scenario setup flow, LARC-016 RADAR active response flow, LARC-017 RADAR integration with Opensearch modules, LARC-018 RADAR logical flow
| Attribute | Value |
|---|---|
| importance | 4 |
| urgency | 3 |
| risk | 2 |
| type | F |
| version | 0.4 |
53 Malware Communication Detection and Prevention: Beaconing SRS-053
As a security engineer, I want RADAR to detect malware command-and-control communication through beaconing patterns and contain the attack using the configured flow.
- RADAR shall emit a C2 alert when it observes beacon-like behavior, i.e. the per-host baseline detector finds a connection with the same destination at nearly regular intervals within the analysis window.
- The alert includes the user/host context, anomaly score and confidence, and time window.
- The Wazuh Monitor sends the alert to webhook upon passing the value of risk threshold.
- If passed the threshold, RADAR executes host isolation as configured: firewall block, service termination and quarantining the host. In the case if the computed risk score is below the threshold, the alert is logged in the index.
- The records of active responses are logged.
Rationale
Regular beaconing to external destinations is a sign of C2 activity, converting it to a scored alert lets RADAR apply the configured containment with an audit trail.
Acceptance criteria
Successful validation according to the corresponding test case specification.
Parent links: MRS-007 Intrusion Prevention
Child links: LARC-015 RADAR scenario setup flow, LARC-016 RADAR active response flow, LARC-017 RADAR integration with Opensearch modules, LARC-018 RADAR logical flow
| Attribute | Value |
|---|---|
| importance | 4 |
| urgency | 3 |
| risk | 2 |
| type | F |
| version | 0.4 |
54 RADAR Automated Test Framework SRS-054
As a security engineer, I want the RADAR test workflow to be automated end-to-end for reproducibly to bring up the stack, feed scenario data, exercise active responses, and collect results without manual steps.
- Automated ingest datasets into Opensearch and create needed users in scenario-specific systems.
- Automated setup of RADAR environment and dependencies.
- Automated threat simulation for testing the functionality of active responses.
- Automated evaluation of the results including the threat simulations with calculated evaluation metrics.
Rationale
It guarantees repeatable setup, realistic data flow, reliable exercising of responses, and consistent evidence (artifacts + metrics).
Acceptance criteria
Successful validation according to the corresponding test case specification.
Parent links: MRS-007 Intrusion Prevention
Child links: LARC-017 RADAR integration with Opensearch modules
| Attribute | Value |
|---|---|
| importance | 4 |
| urgency | 3 |
| risk | 2 |
| type | F |
| version | 0.4 |
55 Geo-based Access Control: Non-whitelisted Country Login Detection and Prevention SRS-055
As a security engineer, I want RADAR to detect access attempts from non-whitelisted countries and apply the existing active response, so that connections from not approved geographies are detected.
- RADAR shall maintain a country whitelist as a machine-readable configuration (e.g., Wazuh CDB list) that can be updated without code changes. The whitelist shall support at least ISO country names or codes consistent with the
srcgeoipfield produced by the GeoIP enrichment pipeline. - For each relevant security event (e.g., interactive logins, VPN sessions, exposed service access), the Wazuh pipeline shall enrich the event with:
srcip(source IP address),srcgeoip(resolved country/region), user identifier, destination service / hostname, and timestamp. - RADAR shall emit a "Non-whitelisted Country Access" alert when the
srcgeoipvalue does not match any entry in the configured country whitelist, and the source IP is public and not part of an internal/private address range. - When the alert is emitted, an active response in the form of email shall be sent to corresponding responsible person.
- The records of active responses are logged.
Rationale
Country-based access control is a practical policy for reducing exposure of critical services to high-risk or non-business-relevant regions. By combining GeoIP enrichment, a centrally managed country whitelist, and Wazuh active responses, we can automatically detect and contain access attempts from non-approved geographies.
Acceptance criteria
Successful validation according to the corresponding test case specification.
Parent links: MRS-007 Intrusion Prevention
Child links: TST-043 RADAR: build non-whitelist GeoIP detection, TST-051 RADAR: build non-whitelist GeoIP detection, TST-058 RADAR: build non-whitelist GeoIP detection with case creation
| Attribute | Value |
|---|---|
| importance | 4 |
| urgency | 3 |
| risk | 2 |
| type | F |
| version | 0.5 |
56 Log volume spike detection per endpoint SRS-056
As a security engineer, I want RADAR to detect unusual log volume spikes for each endpoint based on its own normal behavior, and then apply the existing risk policy to decide how to react.
- RADAR shall emit a "Log volume spike" alert when the detector for an endpoint sees that the number of logs in the current time window is much higher than the learned baseline for that same endpoint, and the anomaly score from the detector is above a configured threshold. The baseline is behavioral and per endpoint (each endpoint has its own “normal” log rate learned from history). Log volume refers to logs produced under the directory
/var/logon each endpoint. - The "Log volume spike" alert shall include: endpoint identity, detector name/ID, time window (start and end), anomaly score and confidence.
- The Wazuh Monitor sends the alert to webhook upon passing the value of risk threshold.
- If passed the threshold, RADAR shall trigger the configured active responses in the form of email alert and logging.
- The records of active responses are logged.
Rationale
Each endpoint has its own “normal” log rate. A strong, sudden spike in log volume for a specific endpoint can mean misconfiguration, abuse, or an ongoing attack. Detecting spikes relative to each endpoint’s own baseline reduces noise and allows RADAR’s risk policy to decide when to alert responsible person.
Acceptance criteria
Successful validation according to the corresponding test specification.
Parent links: MRS-007 Intrusion Prevention
Child links: TST-044 RADAR: build log volume abnormal growth, TST-045 Run RADAR for log volume abnormal growth, TST-052 RADAR: build log volume abnormal growth, TST-053 Run RADAR for log volume abnormal growth
| Attribute | Value |
|---|---|
| importance | 4 |
| urgency | 3 |
| risk | 2 |
| type | F |
| version | 0.5 |
57 Ransomware attack detection and response SRS-057
As a security engineer, I want RADAR to detect ransomware attacks on endpoints through both signature-based patterns and anomalous file system behavior, and then apply the existing risk policy to decide how to react.
- RADAR shall employ a dual-detection approach for ransomware: - Signature-based detection: Monitor for known ransomware indicators including ransom note file creation, suspicious file extensions, and known ransomware process names. - Anomaly-based detection: Detect unusual file system activity patterns per endpoint, including abnormal rates of file modifications, mass file renaming, rapid encryption-like entropy changes, and unusual file access patterns.
- RADAR shall emit a "Ransomware attack detected" alert when either: - Signature-based detector identifies ransomware indicators, OR - RRCF anomaly detector for file system behavior reports an anomaly score above the configured threshold for metrics indicative of ransomware activity (rapid file modifications, entropy changes, extension changes) per endpoint.
- The "Ransomware attack detected" alert shall include: endpoint identity, detection method, detector name/ID, timestamp of detection, anomaly score and confidence, affected file paths.
- For anomaly-based detection, the Wazuh Monitor sends the alert to webhook upon passing the value of risk threshold. For signature-based, the rule should be triggered.
- RADAR shall run the configured active responses for the triggered rule in the form of email alert, case creation, context collection and logging.
- The records of active responses are logged.
Rationale
Ransomware represents a time-sensitive threats to organizational infrastructure, capable of causing complete operational disruption. A hybrid-detection approach is helpful because signature-based detection enables immediate identification of known ransomware families and their artifacts, while RRCF anomaly-based detection identifies zero-day and polymorphic variants by recognizing the fundamental behavioral patterns inherent to ransomware—mass file modifications, rapid encryption, and abnormal file system traversal. This combination provides comprehensive protection across both known and unknown threat vectors, delivering the earliest possible warning.
Acceptance criteria
Successful validation according to the corresponding test specification.
Parent links: MRS-007 Intrusion Prevention
| Attribute | Value |
|---|---|
| importance | 4 |
| urgency | 3 |
| risk | 2 |
| type | F |
| version | 0.7 |