1.0 ADBox subsystem HARC-001
The diagram below depicts the context of the ADBox subsystem.
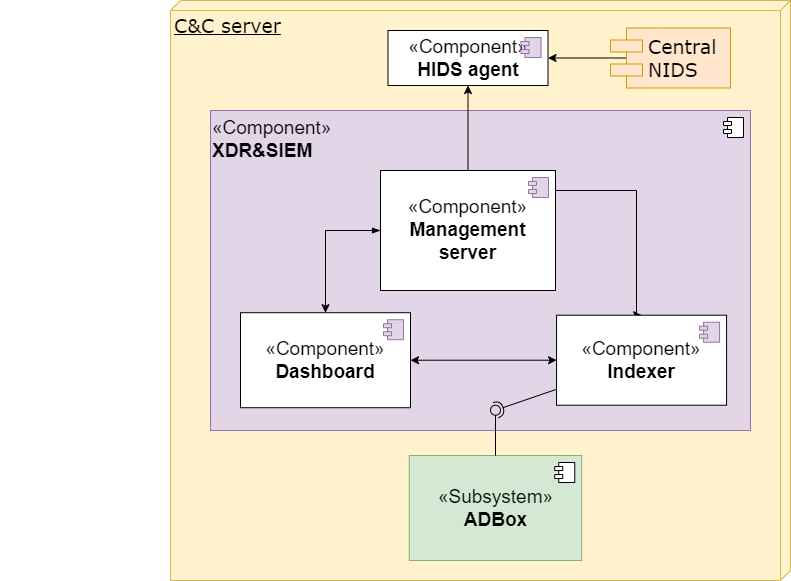
Parent links: MRS-002 Command & Control, MRS-004 Multivariate Anomaly Detection, MRS-032 Host and Network Ingestion, MRS-033 API Data Retrieval, MRS-039 Offline AD, MRS-041 Standalone AD Subsystem
2.0 ADBox architecture HARC-002
The diagram below depicts the high-level architecture of the ADBox subsystem.
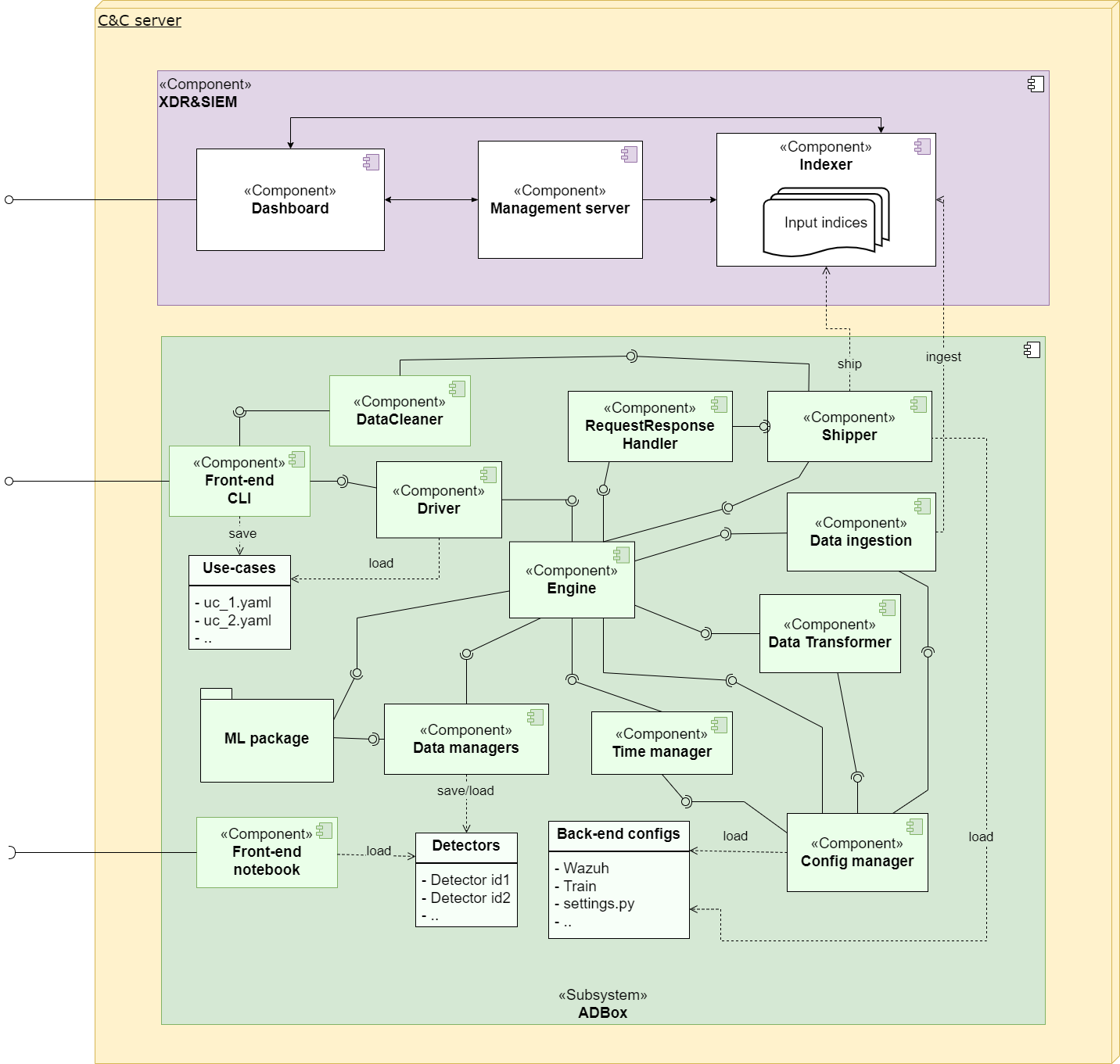
Parent links: MRS-004 Multivariate Anomaly Detection, MRS-031 Multiple ML Techniques, MRS-032 Host and Network Ingestion, MRS-033 API Data Retrieval, MRS-039 Offline AD, MRS-041 Standalone AD Subsystem
3.0 IDPS-ESCAPE context HARC-003
The diagram below illustrates the overall context of the IDPS-ESCAPE system.
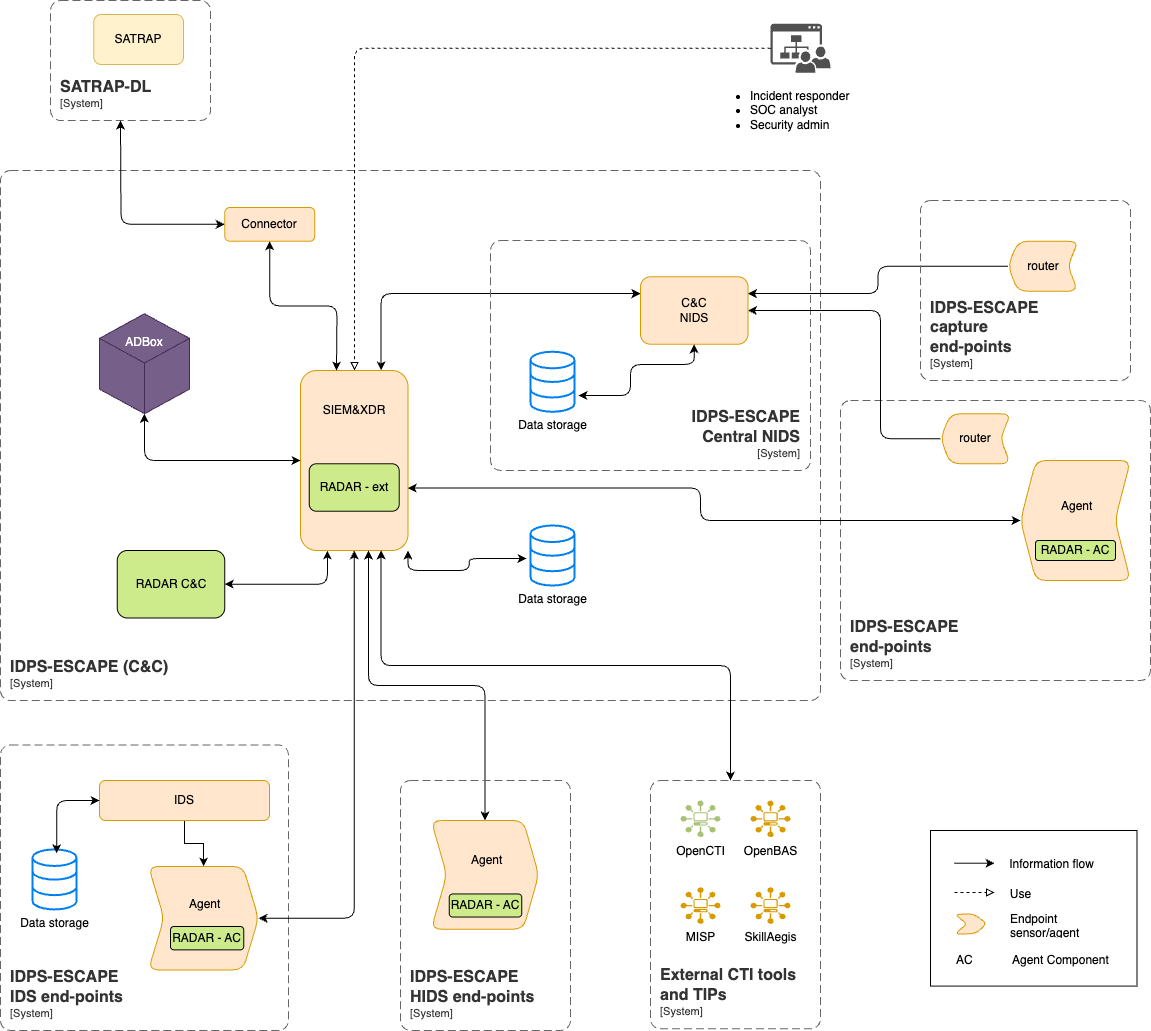
Parent links: MRS-002 Command & Control, MRS-003 Agent Data Centralization, MRS-004 Multivariate Anomaly Detection, MRS-005 Host-based Intrusion Detection, MRS-006 NIDS Support, MRS-007 Intrusion Prevention, MRS-008 Network Capture Forwarding, MRS-011 Signature-based Host IDS, MRS-012 XDR & SIEM Integration, MRS-013 Visual Dashboard, MRS-017 Monitoring Frontend, MRS-018 Data Management Subsystem, MRS-019 3rd-Party Open-source Signature-based NIDS, MRS-020 Platform Independence, MRS-022 Network Endpoint Monitoring, MRS-032 Host and Network Ingestion, MRS-033 API Data Retrieval, MRS-037 Multiple Deployment Models, MRS-039 Offline AD, MRS-040 Signature-Based NIDS, MRS-041 Standalone AD Subsystem
4.0 RADAR architecture HARC-004
The diagram below depicts the high-level architecture of the RADAR subsystem.

Parent links: MRS-007 Intrusion Prevention, MRS-012 XDR & SIEM Integration
5.0 RADAR Automated Test Framework architecture HARC-005
The diagram below depicts the high-level architecture of the RADAR Automated Test Framework.

Parent links: MRS-007 Intrusion Prevention
6.0 RADAR deployment: Remote Agent and Remote Manager mode HARC-006
The diagram below illustrates the RADAR build-time and run-time architecture for a deployment in which both the Wazuh Manager and the Wazuh agents are hosted on remote endpoints.
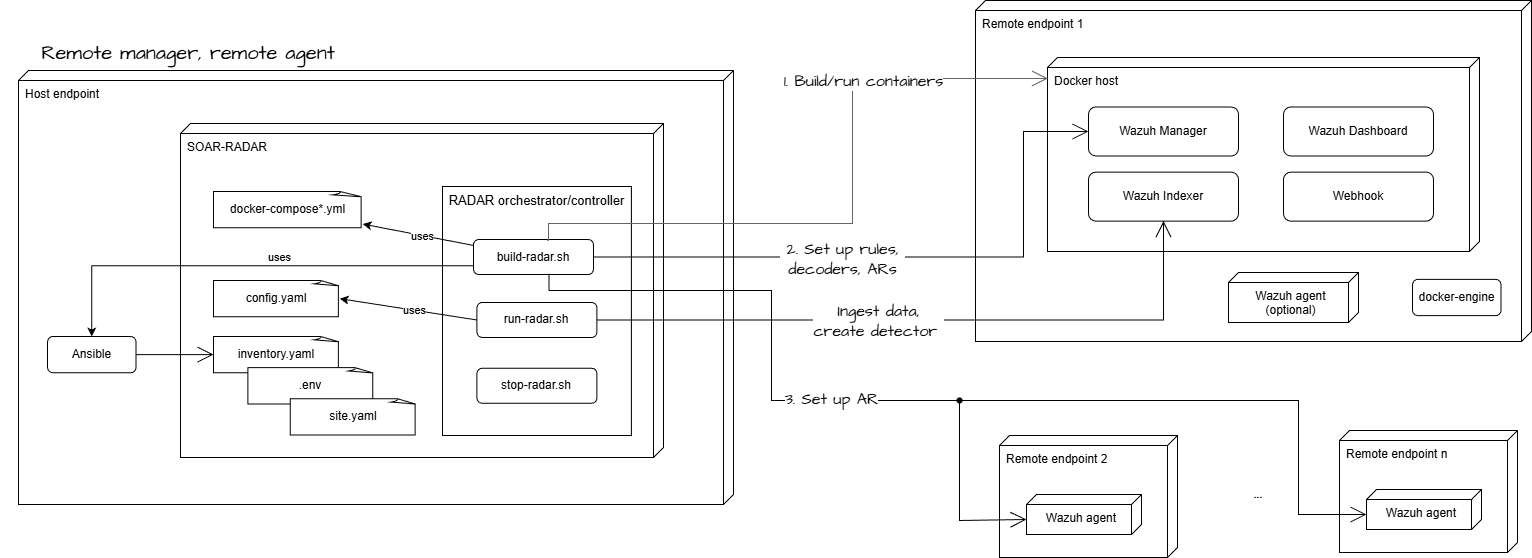
Parent links: MRS-007 Intrusion Prevention
7.0 RADAR deployment: Remote Agent and Local Manager mode HARC-007
The diagram below illustrates the RADAR build-time and run-time architecture for a deployment in which the Wazuh Manager is hosted locally, while the Wazuh agent runs on a remote endpoint.

Parent links: MRS-007 Intrusion Prevention
8.0 RADAR deployment: Local Agent and Local Manager mode HARC-008
The diagram below illustrates the RADAR build-time and run-time architecture for a deployment in which both the Wazuh Manager and the Wazuh agent are hosted locally using Docker containers.
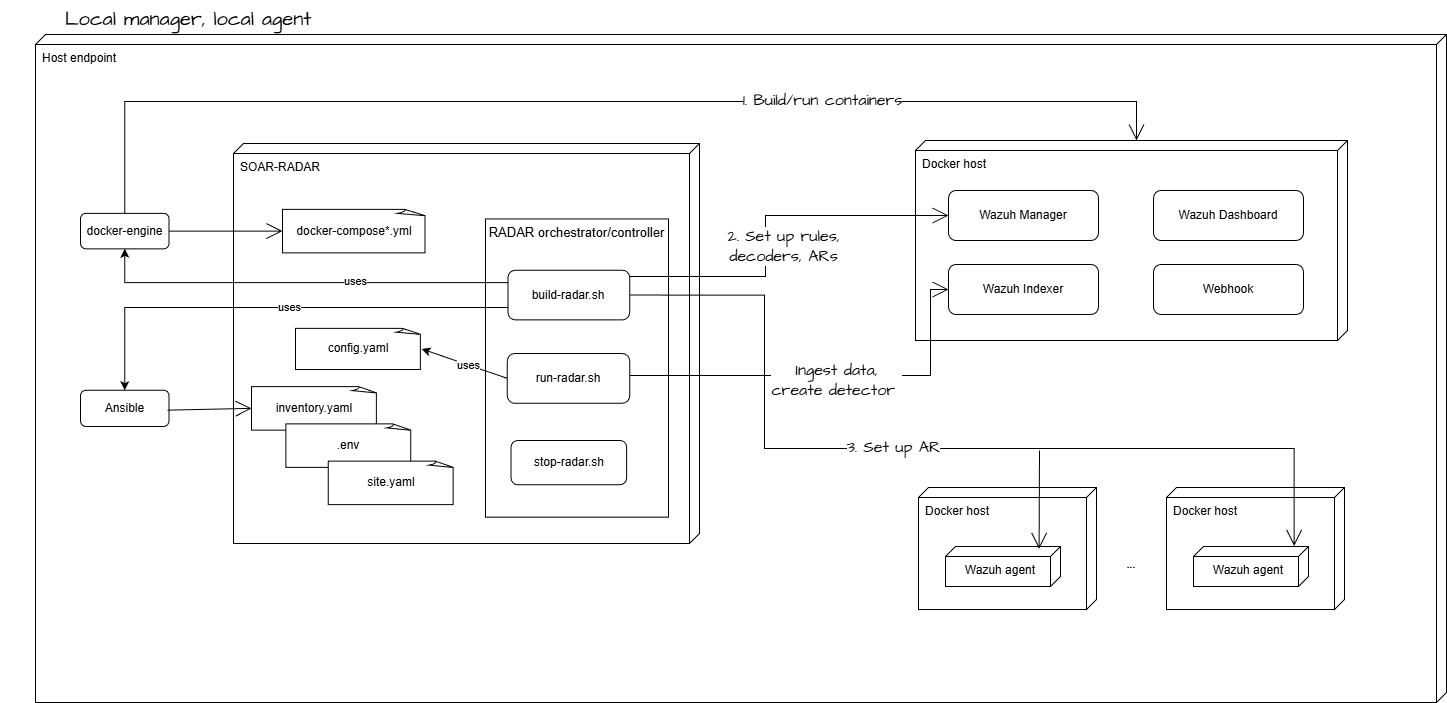
Parent links: MRS-007 Intrusion Prevention
9.0 SONAR subsystem context HARC-009
The diagram below depicts the system context of the SONAR (SIEM-Oriented Neural Anomaly Recognition) subsystem within the IDPS-ESCAPE architecture.
SONAR is a multivariate anomaly detection engine that analyzes Wazuh security alerts to identify unusual patterns that may indicate security threats. It integrates with the Wazuh Indexer (OpenSearch) for data ingestion and result storage.
System boundary
Key interfaces
| Interface | Direction | Protocol | Purpose |
|---|---|---|---|
| Wazuh Indexer API | Inbound | HTTPS/REST | Alert retrieval, query execution |
| Wazuh Data Streams | Outbound | HTTPS/REST | Anomaly document indexing |
| RADAR Webhook | Outbound | HTTPS/REST | Real-time anomaly notifications |
Related documentation
- Technical architecture:
docs/manual/sonar_docs/architecture.md - UML diagrams:
docs/manual/sonar_docs/uml-diagrams.md
Parent links: MRS-032 Host and Network Ingestion, MRS-039 Offline AD
10 SONAR component architecture HARC-010
The diagram below depicts the high-level component architecture of the SONAR subsystem.
Component diagram
Component responsibilities
| Component | Responsibility |
|---|---|
| cli.py | Command-line interface, argument parsing, workflow orchestration |
| scenario.py | YAML scenario loading, validation, configuration merging |
| engine.py | MVAD engine lifecycle, training/detection execution |
| pipeline.py | Post-processing, anomaly document creation, result formatting |
| features.py | Feature extraction, time-series bucketing, data transformation |
| wazuh_client.py | Wazuh Indexer API communication, alert retrieval |
| local_data_provider.py | Debug mode data provider (JSON file loading) |
| shipper/ | OpenSearch data stream management, bulk ingestion |
| config.py | Configuration dataclasses, type definitions |
Related documentation
- Detailed architecture:
docs/manual/sonar_docs/architecture.md - Component diagram:
docs/manual/sonar_docs/uml-diagrams.md#component-diagram
Parent links: MRS-032 Host and Network Ingestion, MRS-039 Offline AD
11 SONAR data flow architecture HARC-011
The diagram below illustrates the high-level data flow through the SONAR subsystem for training and detection operations.
Training data flow
Detection data flow
Data transformations
| Stage | Input | Output | Transformation |
|---|---|---|---|
| Ingestion | Wazuh alerts (JSON) | Raw event list | Filtering, time-range selection |
| Feature Engineering | Raw events | Time-series vectors | Bucketing, aggregation, encoding |
| MVAD Processing | Time-series vectors | Anomaly scores | Multivariate analysis |
| Post-Processing | Anomaly scores | Anomaly documents | Thresholding, enrichment, formatting |
| Shipping | Anomaly documents | Indexed records | Bulk ingestion to data streams |
Related documentation
- Data flow diagram:
docs/manual/sonar_docs/uml-diagrams.md#data-flow-diagram - Architecture details:
docs/manual/sonar_docs/architecture.md#data-flow
Parent links: MRS-032 Host and Network Ingestion, MRS-039 Offline AD